5 Security Blindspots
No buzzwords or Gartner categories, just really important security stuff
As a reminder, this post is not sponsored in any way, and these vendors don’t even know I’m talking about them this week.
I talk a lot about buzzwords that I think are important - most recently ASPM (all encompassing application scanning) and ADR (cloud + application runtime, more on that next week!). While these are the two areas where most attention is currently focused, many companies already do some kind of vulnerability scanning and some kind of runtime defense.
This article aims to address 5 areas security teams struggle to gain visibility into, and the vendors who are tackling them (despite the lack of clear Gartner categories for their work).
These areas are:
User granted cross service authentication (OAuth)
Third party data flows out of your environment
Implementing security features into your application (like checking for common passwords)
A perimeter approach to cloud identities
Creating relationships with open source maintainers
1. Securing OAuth - Astrix Security
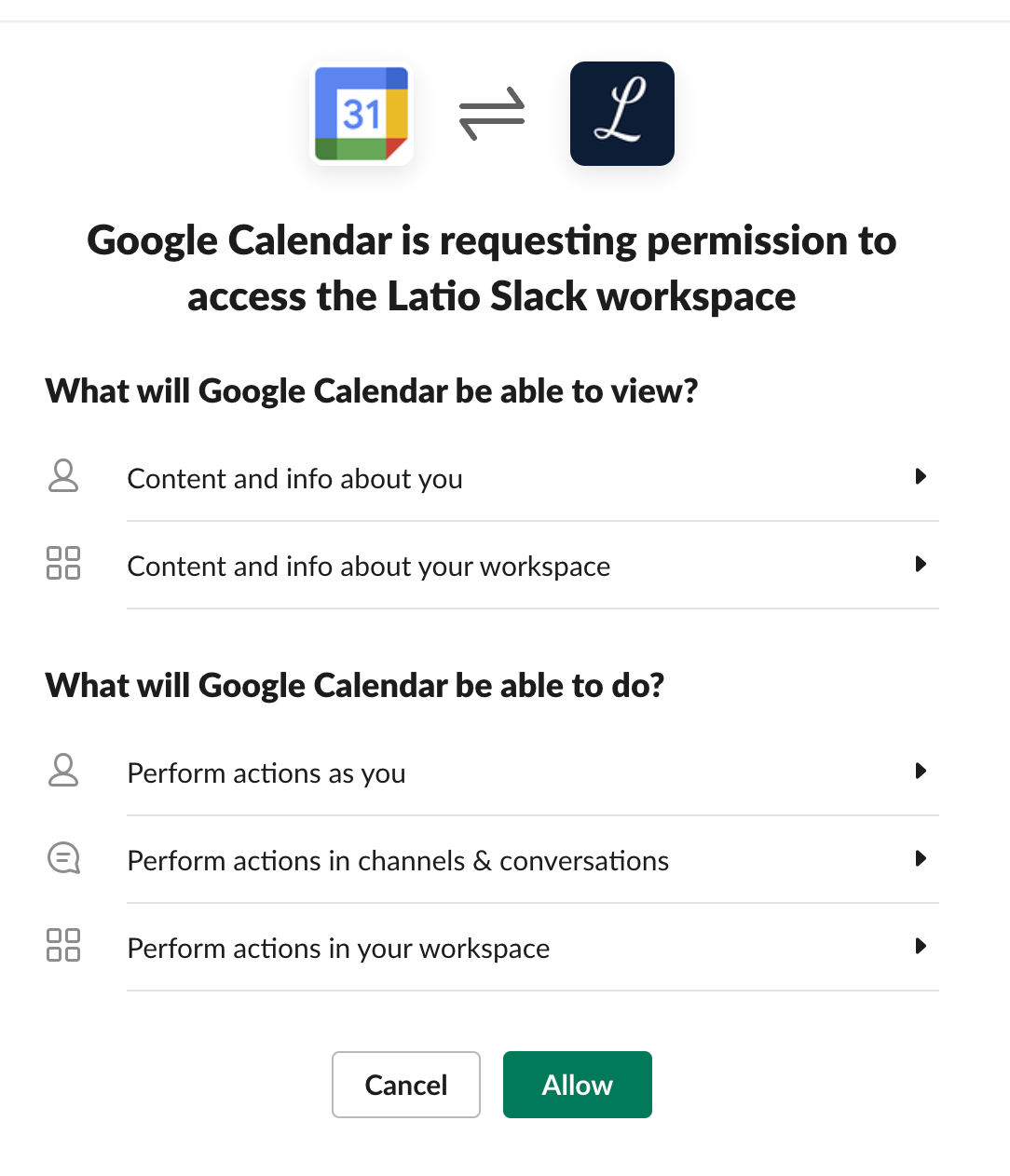
Whether you know it or not, you and your employees are using “OAuth” to access applications dozens of times a day. OAuth security is best explained via a use case: let’s say you’re adding the Google Calendar Application into your Slack environment. You’ll be hit with a screen like this:
This connection is done via OAuth, and it’s an overlooked aspect of security because end users usually have an unregulated ability to create connections between their applications. The non-nerdy description of what’s happening here is you’re granting Google a key to access your Slack environment. That key has the ability to do some specific things you’re authorizing it to do - like send messages to a described channel when you have a calendar event, or read messages where you summon the bot.
Let’s say that key suddenly starts creating new third party connections, or adding additional members to your org, or posting messages to unauthorized channels. That’s interesting for two reasons: first, it let's you know, before Google even tells you anything, that you may have a third party compromise going on, and allows you to quickly disable the key and audit what happened. Second, it allows you to tell Google they may want to look into their Slack application.
Because these third party connections take very predictable actions across multiple environments, Astrix had the great idea to baseline and monitor these actions across their customers. This allows them to provide a huge amount of visibility, detection, and response, into an aspect of security that’s long been overlooked.
2. Data Flow Visibility & Enforcement - Riscosity
While there are a ton of tools out there that say they monitor where your “sensitive data” lives and goes, 99% of them are lacking in some fundamental way. You might have a DSPM that tells you where sensitive data is, you might even have controls around viewing that data, but almost no one has real visibility into their third party data flows.
Despite the lack of maturity in this space, most security teams have some home grown attempt to track which vendors access which types of data - usually in the form of a spread sheet. This spreadsheet is usually wildly out of date, and doesn’t track the numerous hidden APIs that your developers are exchanging data with as part of making your app work.
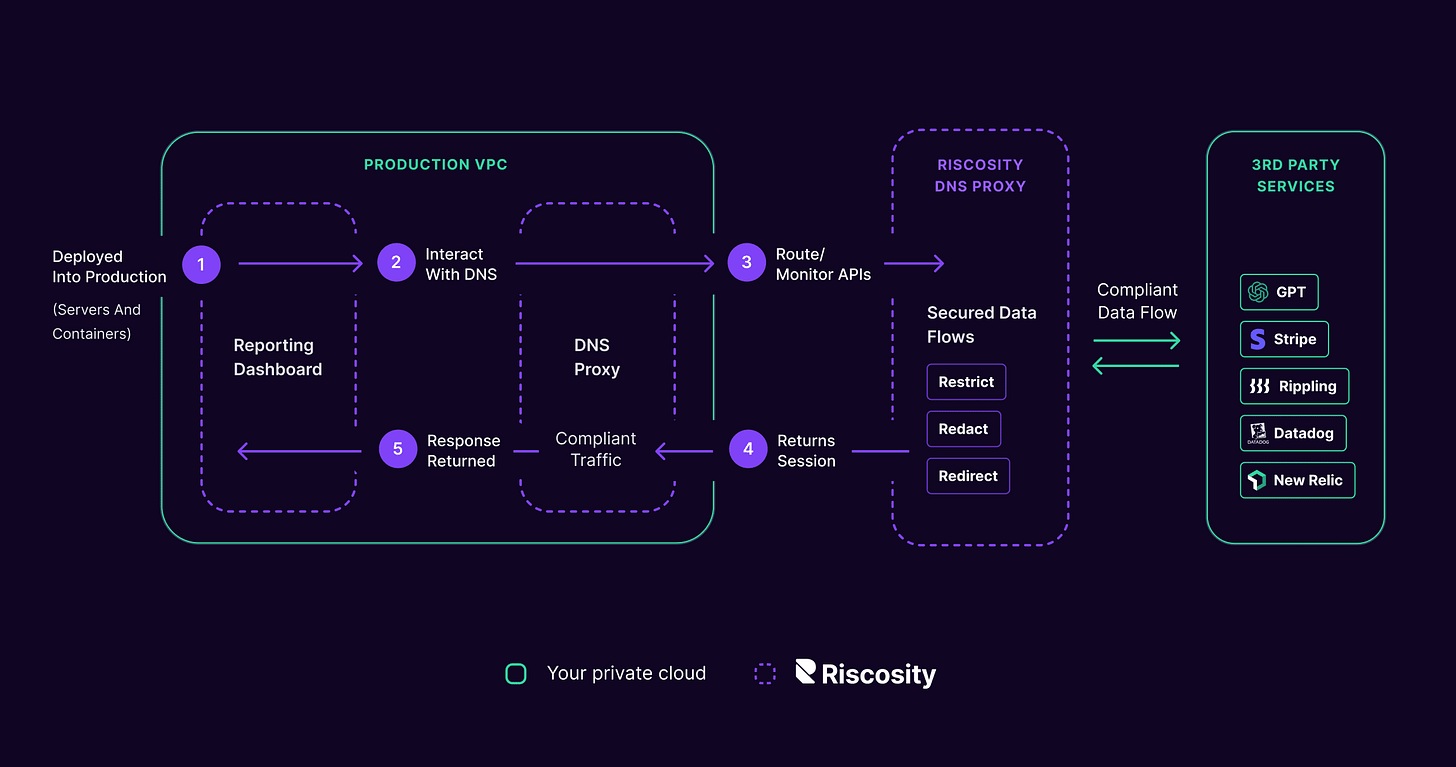
What makes Riscosity unique is their ability to get visibility into data flows from the code, and then validate that with runtime - all without an agent or code changes. This is data every compliance or security team would love to have, but we don’t think it’s really possible because of the number of half hearted solutions out there claiming to do this without any real visibility into applications.
While most compliance teams might maintain a list of “trusted third parties” and maybe even “vendors” used in development, I’m certain they would be shocked to see the picture of reality - where developers are importing SDKs (read: APIs) from an unbelievable number of third party providers. Riscosity uniquely gets visibility into this from both sides - where data should be going from the code, and where it actually is going from the network. To top it off, they do it with an elegant network level change, which makes it way more achievable than major code changes or agent deploys.
3. Security Features SDK - Pangea
Unfortunately, many security teams are so swamped in operations they don’t have time to think through application security issues with their developers beyond begging them to fix vulnerabilities. Usually, the concerns Pangea deals with comes up when compliance gets a questionnaire asking, “do you enforce password complexity in your application?” and the answer is “uh, I think so?”
Until Pangea, there really hasn’t been a standardized way to implement some security features into your application. Things like malware scanning user file uploads, scanning url’s shared publicly, and checking threat feeds have been hacky one off solutions that may or may not offer SDKs.
Pangea offers a simple solution to hand off to developers to empower them to add some great security features for your end users, without the typical research trade offs that make this stuff time consuming to implement.
4. Cloud Identity Perimeters - InstaSecure & Sonrai
If we’re honest, least privileged access has been a better idea than reality in the cloud. While defining permissions as granular JSON allow a theoretical perfect level of security, the complexity of maintaining these policies have created unrealistic standards.
Said differently, if your company is struggling with access reviews (like we all are), then you’re definitely not keeping up with cloud policy reviews. The Just in Time Access (JIT) approach has remedied a lot of the risk here - granting permissive roles during incidents or only for the duration that they’re needed; however, this itself is also not a solution for people doing most of their day to day work.
Sonrai and InstaSecure are both helping companies implement simple boundary based solutions - it’s a lot easier to say shouldn’t be happening instead of declaring exactly what should be. Sonrai is focusing on a simple one click addition to enforce helpful boundary controls against unused resources and extremely sensitive permissions - this is a thoughtful approach to permissions boundaries. InstaSecure is helping with the data perimeter approach, enforcing controls around where data flows should and shouldn’t be happening.
Both tools offer an easier solution to cloud identity management than trying to universally enforce and audit least privileges. I think the future of cloud identities will be JIT access paired with a robust boundary.
5. Open Source Support - Tidelift
FedRAMP guidance on when you don’t have to remediate vulnerabilities on time is actually pretty accurate, there are four categories for not meeting timelines: Risk Adjustments, False Positives, Operational Requirements, and Vendor Dependencies. It says a lot that open source libraries are called “vendor dependencies” - but the maintainers just don’t know it! What kind of vendor is that!?
Every vulnerability scanner out there, even the ones with the best reachability and workflows, have a core problem: a patch needs to be available for you to do anything about it. Only Tidelift helps you treat open source maintainers as actual vendors (instead of pretending they are). This comes with the benefit not just of doing what’s morally right, but of guaranteeing support for the open source applications that otherwise are just arbitrarily trusted dependencies.
Let me put it this way: if you have a team dedicated to reviewing and authorizing vendors before you purchase them, why would you blindly approve open source vendors who have far greater visibility and impact into your core business functions? Tidelift just makes the process better for everyone.
Bonus Mentions: Permiso, Phylum, Query, Moderne, & Grit
There are more vendors doing cool stuff than I can consistently talk about, here are 5 more I don’t talk about enough tackling some big real security problems.
Permiso provides runtime identity detection and response - a critically overlooked aspect of stopping attackers.
Phylum has the best threat feed and most dedication to open source malware detection. Their research blog is fantastic.
Querying logs is the heart of security operations, and Query offers a fantastic solution for maximizing your ability to access it.
The hardest part of fixing vulnerabilities are deploying large scale framework upgrades across major versions. Moderne and Grit both have their own flavor helping accomplish these major migrations.