Unpacking Wizdom and GitHub Universe 2025
What the announcements mean for the future of cloud and application security
Over the last two weeks I attended user conferences for two of the biggest presences in cloud and application security - GitHub and Wiz. Both conferences demonstrated smart leadership decisions, filling feature gaps with competitors alongside delivering innovations that highlight their platform’s strengths. In this article, I’ll cover both the product announcements and what these investments signal for the industry.
GitHub
At their user conference, GitHub showed agility in opening up their platform to third party LLMs, and a new focus on enabling AI code generation at enterprise scale. Additionally, many experimental features launched: from kicking off copilot workflows from Slack conversations, to using copilot to fix vulnerabilities. GitHub also showed continued focus on enterprise management features, enabling the product to work better at scale.
Bringing AI to Enterprise
The overarching theme of GitHub’s releases across security and the rest of the product were bringing AI coding tools to enterprises. It’s no secret that AI code generation has the strongest product market fit in AI, and it’s awesome to see GitHub immediately moving to deliver these features to large enterprises.
While tools like Cursor, Codex, and Claude Code are getting the benchmark attention, the reality for the average enterprise developer is much more restricted. Startups can freely experiment with almost any AI CLI tool that gives the best results and vibe code their minimal viable product, but enterprise teams have to approach the adoption of AI tools responsibly and at scale across massive, complex codebases.
In order to enable deploying AI tools at scale, most of GitHub’s non-security announcements were providing ways to solve management challenges with managed rules, custom agents, and knowledge bases across distributed teams and repos. GitHub is allowing teams to bring their own models, agents, and workflows to copilot, while giving managers the ability to orchestrate these tools across their enterprise, safely.
From a UX perspective, there’s an unavoidable tension between cloud based and local agentic coding flows, e.g. calling copilot via Slack to open a PR, versus using copilot CLI on a developer machine. GitHub is taking steps towards unifying these experiences, allowing developers to more easily navigate between branches as some coding tasks are completed locally, and others in the cloud through VSCode. Their early experimentations with custom agents and knowledge bases are essential to making the cloud only PR experience a reality.
Copilot Workflows Introduce a New Way to Scan
Now that AI code generation workflows can be kicked off asynchronously, GitHub is introducing a CodeQL analysis step that fits directly into the code generation process. For cloud based copilot generation workflows, CodeQL will get called as part of the pull request, checking for SAST vulnerabilities in the generated code. Copilot will then remediate any findings. GitHub is bringing these capabilities first to cloud generated code where the UX challenges will be less apparent. On the one hand, this promises a future where code security happens before the developer even sees the code. On the other, I haven’t found the workflow of calling a SAST tool via MCP to lead to great results when testing other tools.
The more fundamental threat GitHub’s releases pose to the application security industry is baking secure coding practices directly into the code generation workflow. AI coding is rapidly opening a new generation of what “shift left” means, as baking into the IDE becomes more about being baked into the context window itself. This shift is already hitting the market from companies like Backslash and Arnica, whose rules management approaches help developers produce secure code, without interrupting their workflows. I’ve been extremely impressed with some early hands on time comparing code generated with and without these tools.
Code Quality Rules
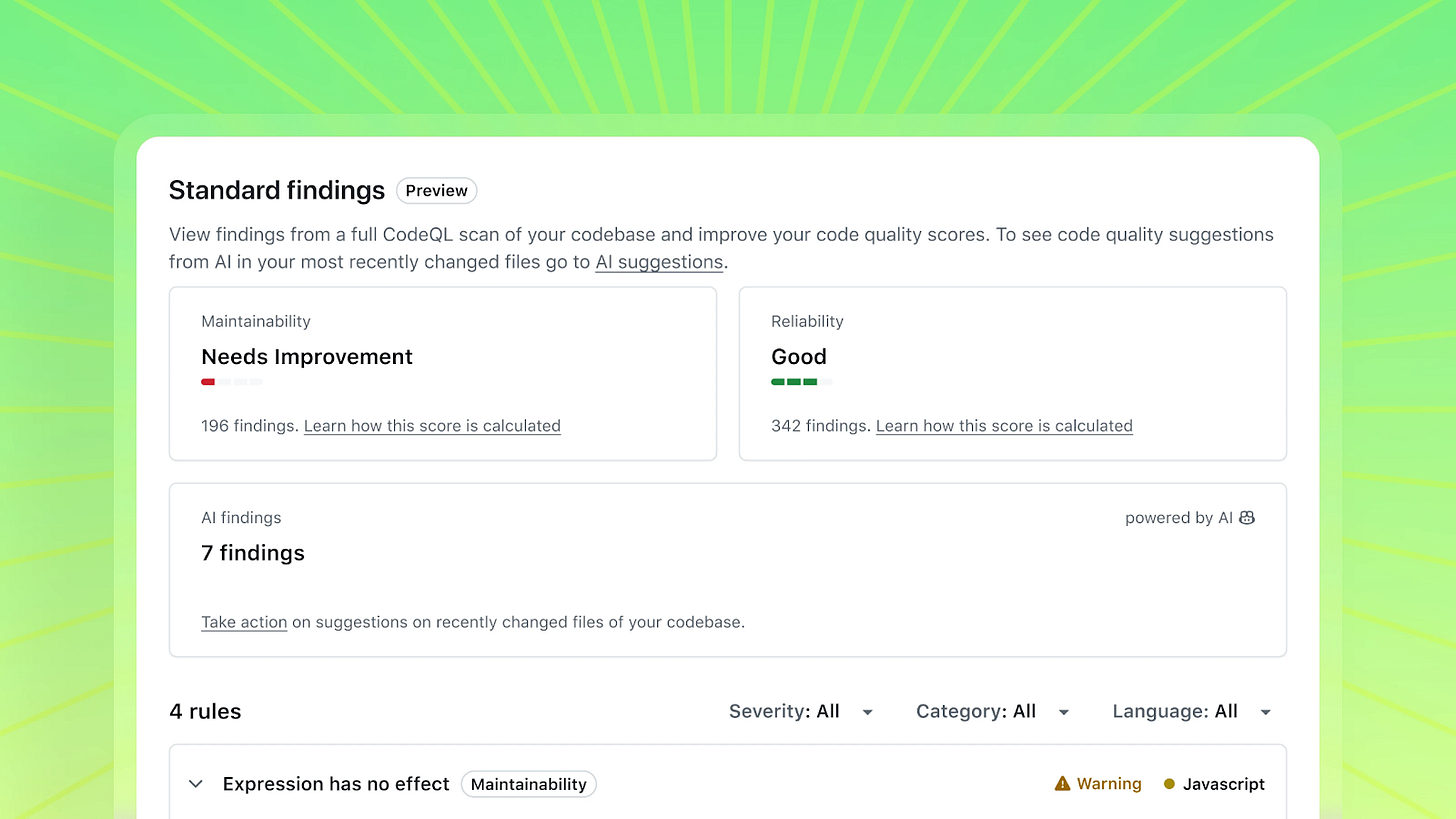
In addition to CodeQL running on AI generated code, the other major scanning announcement was the introduction of code quality rules, also using CodeQL. While the code quality feature seemed early, lacking code coverage and clear management workflows, many teams are more than happy to migrate off their legacy code quality tools and get a more unified solution. This allows GitHub to join the surprisingly few vendors that offer unified code quality and security solutions: Sonar, Aikido, and Codacy. For a long time end users have wanted these tools consolidated, but vendors haven’t quite delivered the maturity needed across both sides to completely win both end users over. As a developer tool first, it seems likely that GitHub takes the necessary steps to mature this solution.
Alongside these major announcements, most of the product improvements continue to make GitHub Advanced Security enticing to teams who may prefer the management features of standalone solutions. GitHub’s management capabilities have come a long way in the last year, adding features like internet reachability from Microsoft Defender and importing Sarifs from third parties. GitHub seems to be investing in expanding their partnership capabilities, getting data in and out of the platform more effectively to enhance vulnerability workflows. All of these releases point to making GitHub a more enterprise friendly and connected platform.
Wiz
As we covered in the Cloud Security Report, it’s clear that cloud security is evolving beyond the traditional set of CNAPP features and Wiz’s announcements reinforce this. During Wizdom they defined two clear goals: continued cloud security leadership, while expanding their footprint across a company’s broader security stack - from traditional vulnerability management to attacks surface management.
Goal 1: Continued Cloud Security Leadership
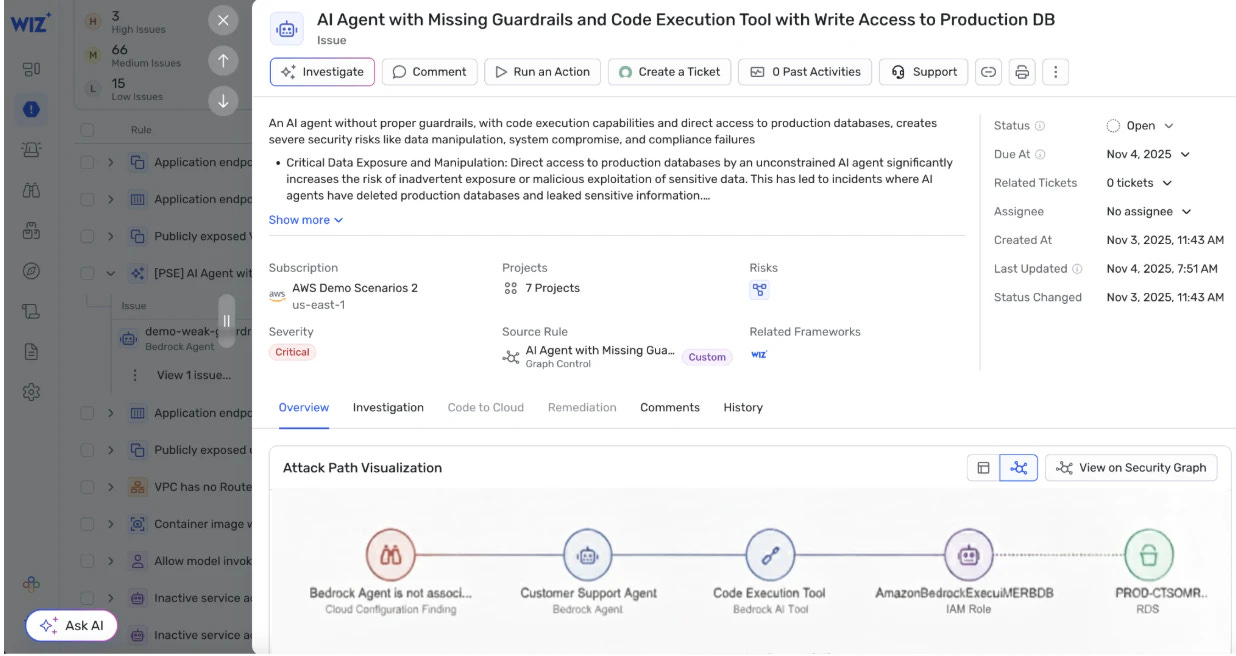
First, Wiz expanded their agentless threat detection capabilities into workloads. By checking network and application logs on disk, Wiz is now providing agentless runtime detection that goes beyond looking at cloud logs alone. While this approach doesn’t spot or stop attacks in real time, it’s a clever addition to agentless scanning capabilities. For workloads that customers can’t deploy agents on, this provides meaningful new visibility and defense capabilities.
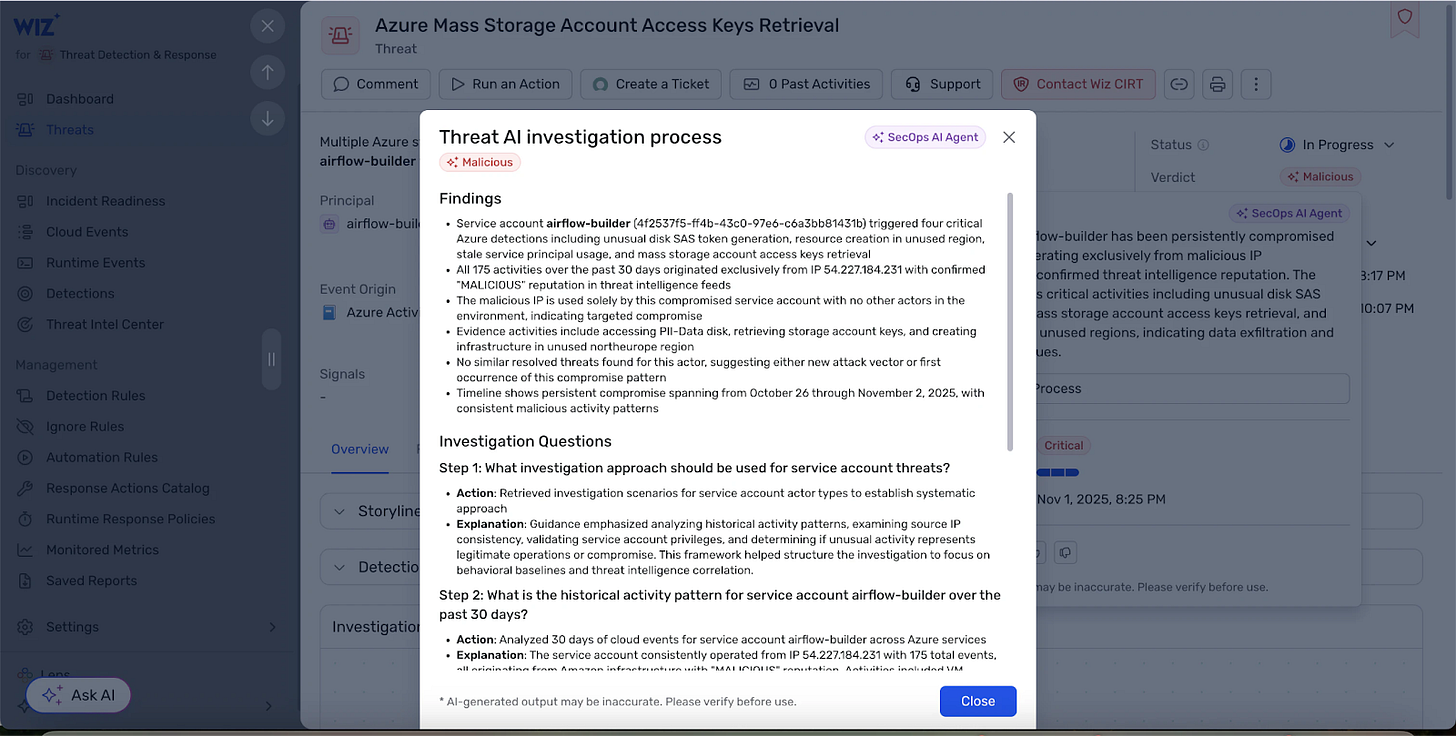
When it comes to their introduction of AI to the cloud security offering (both in terms of securing AI and using it to enable defenders) Wiz has stayed competitive with other providers. Their posture discoveries (AI-SPM) are the most ahead of competitors, extending toxic combination discoveries through to Bedrock configurations and sensitive data flows. For enabling defenders with AI, summaries now exist for Defend issues, but the grouping isn’t as mature as I’ve seen elsewhere.
Wiz is also offering two AI agents: one focused on accessing and fixing issues, and another on incident response. I was able to do a hands-on workshop with MCP and the SecOps flow, and unfortunately like most AI use cases, the value was mixed. Sometimes I was able to one-shot some cool investigations, and at other times the agent would get stuck in a loop trying and struggling to accurately navigate the MCP tools calls. These are limitations I’ve experienced in most of my MCP usage and stem more from the client side than anything with the MCP tools themselves, but as the technologies improve, Wiz’s support for the capabilities will become more essential. The lead here is Wiz’s sophistication in rolling out MCP at scale with safe authorization flows for enterprises.
Goal 2: Entering New Markets
Beyond their core offering, Wiz has also rapidly extended into other markets - from ASM to SaaS security.
First, there’s entering the SaaS security market with a powerful Microsoft 365 integration. This extends the Wiz graph beyond current SaaS integrations like Github and Snowflake, to include workplace identities, file types, and threat detection. While at this point it’s not a full SaaS security platform, Microsoft 365 is at the heart of these tools. While Wiz’s offering wouldn’t be enough to replace a SaaS security solution, it will be a strong offering for teams who haven’t invested in that market.
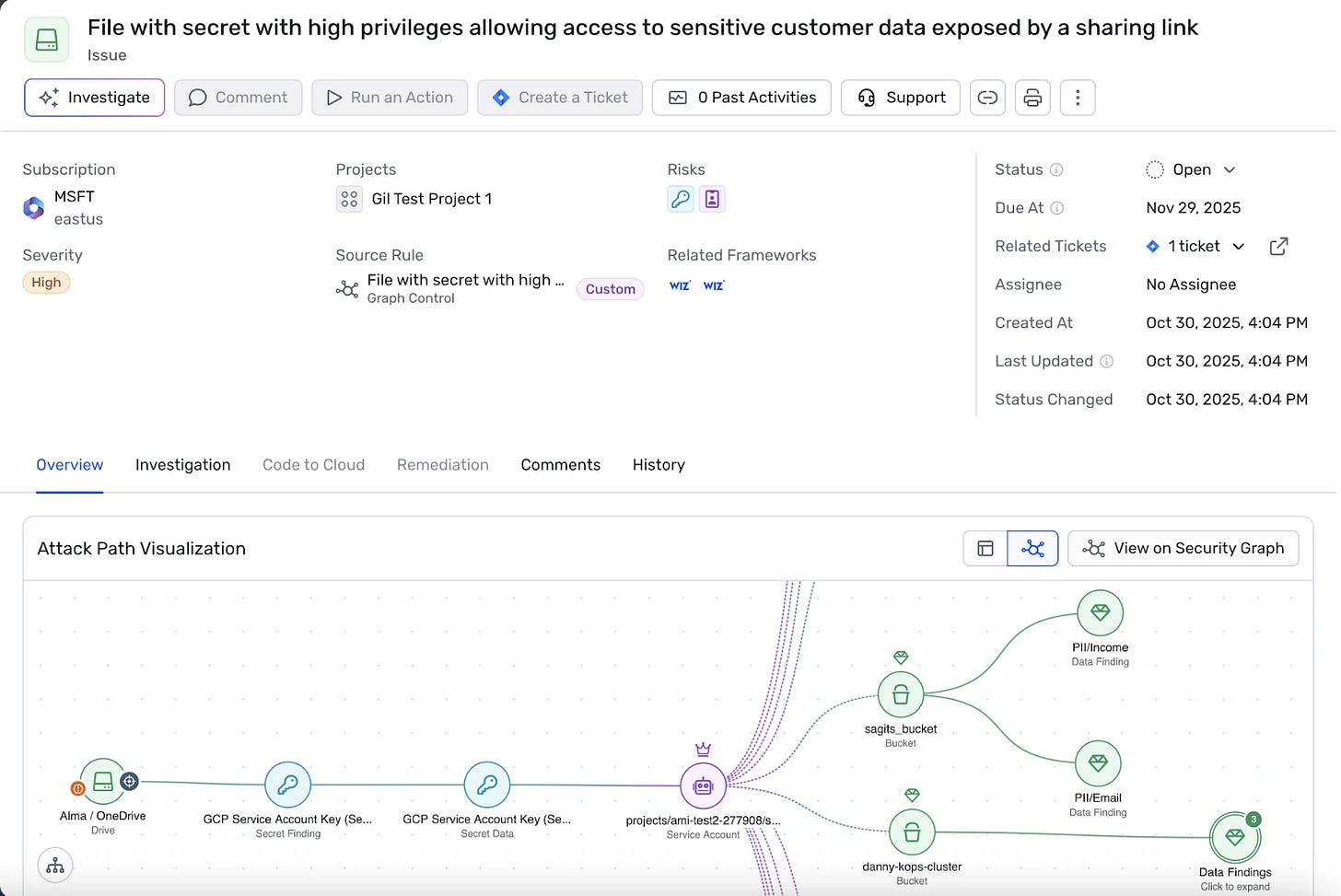
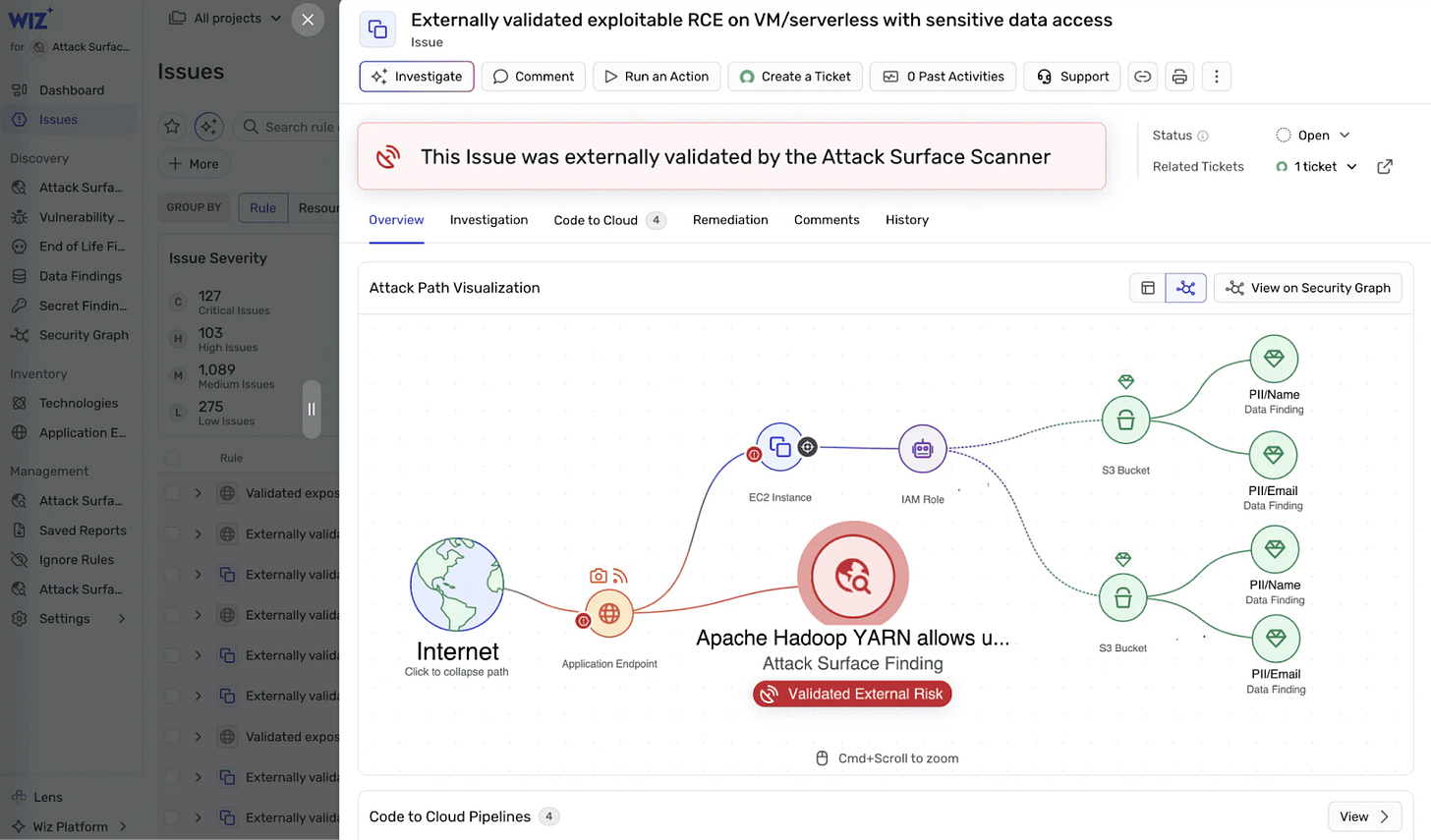
Next, cloud security is quickly evolving into a larger vulnerability management project. Wiz’s release of ASM as a standout offering is a smart move towards this holistic future. For a long time, Wiz has done basic validation of external facing endpoints, providing screenshots of what the web application looks like from the outside. With ASM, they’re beginning the evolution towards a more robust testing solution that will likely lead to full external scanning - from DAST to Nuclei scanning styles. This moves Wiz towards providing end to end validation of if a vulnerability is exploitable.
For Wiz customers, this means that Wiz is delivering more actionable findings across your cloud, building upon the already great posture capabilities. Whether integrating third party tools, or deploying sensors on-premise, Wiz can now be used as a management platform for vulnerabilities across on-prem and cloud. Additionally, security leaders and practitioners wanting to experiment with the value of AI in their programs should encourage their teams to try the MCP integrations for themselves. While I found them of mixed helpfulness in my hands on time, the times it does work feel magical and are a glimpse of what future workflows will look like.
In many ways, Wiz’s feature investments capture the shift of the entire industry, where cloud security platforms are pivoting from a siloed function to a unified platform, and that the future of cloud security has left CNAPP behind.
Conclusion
Wiz and GitHub’s events demonstrate how cloud and application security solutions are evolving: application security is moving towards securing AI code generation, while cloud security is moving towards unified vulnerability and exposure management. What’s remarkable about both companies is their ability to execute on these developments at a large scale - a testament to letting strong teams continue building even in the midst of acquisitions.





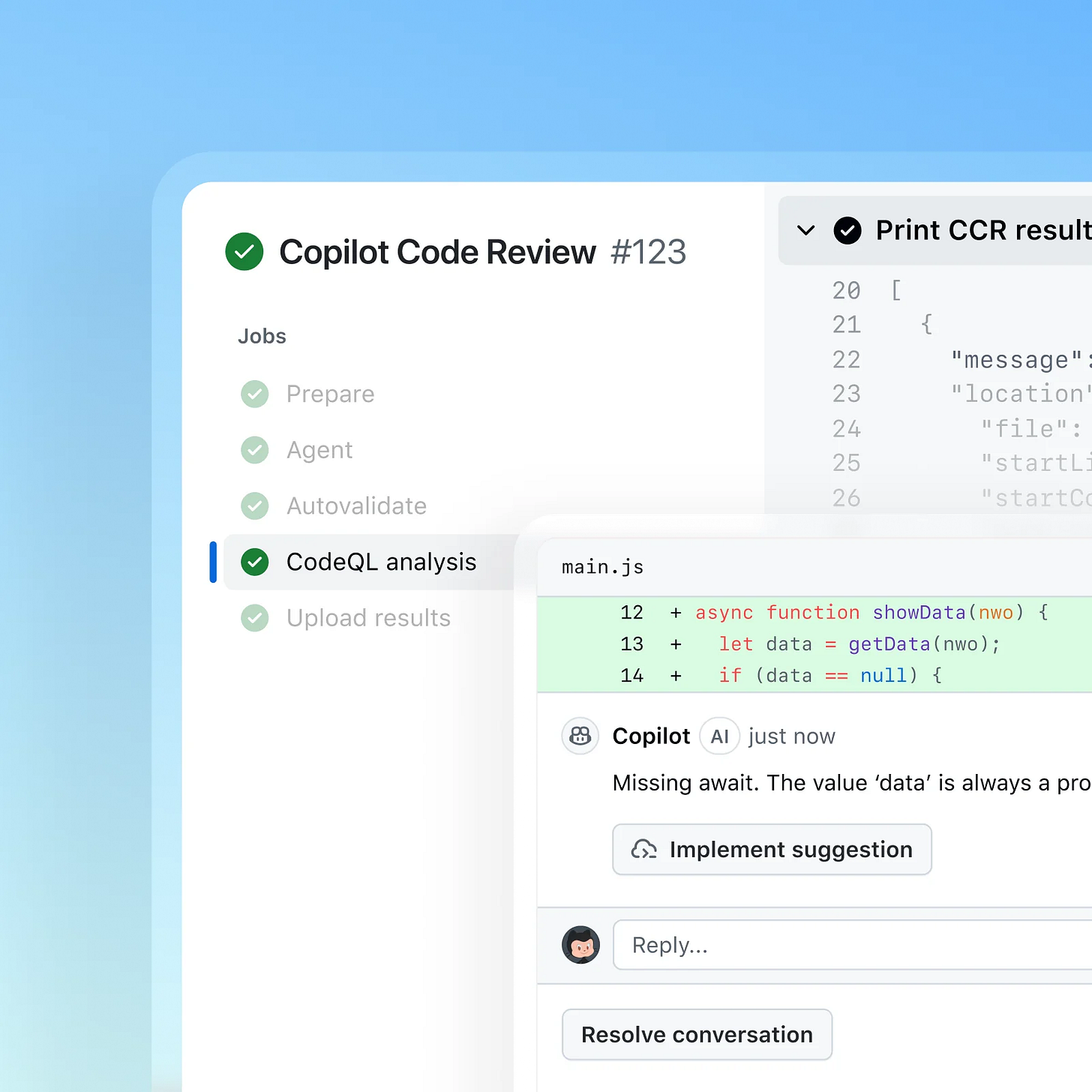
"For cloud based copilot generation workflows, CodeQL will get called as part of the pull request, checking for SAST vulnerabilities in the generated code. Copilot will then remediate any findings. GitHub is bringing these capabilities first to cloud generated code where the UX challenges will be less apparent. On the one hand, this promises a future where code security happens before the developer even sees the code. On the other, I haven’t found the workflow of calling a SAST tool via MCP to lead to great results when testing other tools."
It was great to meet you at Universe and have a deeper chat about our new features 🔐. Awesome to see our momentum reflected in your write-up 🤩.
I do agree that a simple MCP call rarely leads to good results. That's why we've baked all of our security checks (CodeQL, dependency vulnerabilities, secret scanning, and code review) into Coding Agent's underlying platform, invoking some of them at deterministic checkpoints, and some throughout the agent workflow - for all Coding Agent runs - even custom agents. We see this lead to much better outcomes in production than bolted-on solutions, and we've got plenty of ideas on how to improve this even further as we build out the agent platform 🚀.