What do I think about Wiz Code?
Answering my most received question from the last 2 weeks
I wanted to be really careful before talking about Wiz Code. On the one hand, I’ve heard some decry the end of standalone AppSec products just from its announcement. On the other hand, there’s not much that’s actually new with it - imagine if the announcement was just “Wiz has SCA scanning now 🥱.” The truth of what this offering is, is somewhere in between - it’s definitely not a complete ASPM, but it’s also not the bolted on scanner most CNAPPs have trained me to expect. As much as I would love the street cred that would come with being a Wiz hater, there’s just nothing to hate with Wiz Code. In fact, it’s really good.
Before we get started, as a reminder, I have taken $0 from any CNAPP provider ever. I have personally used or evaluated almost every major player in the space. Also, on a personal note, as tired as you are of reading about Wiz, I’m also super tired of talking about Wiz. I am dying for another CNAPP provider to compete with them, but the underlying data architecture and UX of Wiz is just such an advantage to them that it’s difficult to see how others will catch up (a billion dollars cash helps too!). I’m writing this article simply because I have been bombarded by questions asking what I think about Wiz code and what it means for the industry, but I wanted to wait until I saw the product to talk about it.
In this article, we’ll try to cut through the marketing stuff and let you know explicitly what Wiz Code is and what’s new about it. We’ll then talk about what’s good about it, and then the hidden deficiencies that make it not quite the of AppSec.
If you stop reading here, here’s the takeaway: Wiz has a real shot of pulling off the CNAPP nightmare, largely because they’ve ignored letting Gartner build their roadmap for them. Wiz Code is the best offering from a CNAPP, better than some legacy scanners, but not as good as modern ASPMs.
What is Wiz Code?

To summarize the Wiz code offering, it’s three things:
SCA, IaC, and Secrets scanning at the repo level with a GitHub app integration (no pipeline changes required). No I’m not going to count sensitive data and malware scanning as new scanners.
Code to cloud tracing with the WizCLI image validation.
Ingesting SAST and DAST findings from other providers (only Checkmarx SAST natively at the moment, but you can bring your own).
Three thoughts on these broad features:
The scanners focus on the “features as checkboxes” approach. For example, having SCA scanning is one thing, but specific approaches end up making huge differences, such as how vulnerabilities are rolled up, reachability, upstream malware detection, and the list goes on. It’s those little details that make the scanners go from noise generators to things you can actually fix.
This is why I didn’t react much to the initial announcement - Wiz has always sort of had SCA via the CLI scanner, as well as IaC scanning. So at face value, the only thing changing here is adding a few bells and whistles like basic repository only secrets and malware scanning.
The real innovation here lies in the elegance of presenting the new data. Wiz is absolutely maximizing the value of code data into their existing architecture.
Here’s James’ complete list of what’s new, with an emoji indicating how I feel about it. Note: this is in the context of how I feel about these features generally, not about Wiz now having them. In other words, other AppSec vendors (and some CNAPPs) have had these for a while, so I’m not saying I’m blown away that they exist in Wiz as some massive innovation. Instead, this is meant to help understand if something’s worth being excited about or not.
🤩 “Pipelineless Scanning” - Scanning repos via Github integration rather than requiring instrumentation in pipeline
🥱 SCA Scanning without static reachability
🥱 SBOM Generation
🥱 Sensitive Data, Secrets, and Malware
🥱 IaC Scanning
🤩“Threat Detection” looking for suspicious repo changes
🤩Revamped policy engine allowing actions to take place based on scanning at code, build, or runtime
🥱Runtime reachability via the Wiz agent (loaded vs. unloaded, not function level like Oligo, Raven, Sweet, or Kodem)
🤩Code to Cloud graph, users can click a vulnerability in production and see the repository and docker file it came from
New workflow stuff
🥱Opening pull requests for remediation
🥱IDE plugin to tell you to change the “1” to a “2” in your Dockerfile
Vulnerability de-duplication
🤩 This is the super star of the whole thing, the elegance of switching between vulnerabilities discovered in code and in cloud, and being able to create developer dashboards from those searches
API for vulnerability ingestion
🤩 “Toxic Combos” based detection combining code context into the overall attack path
Final Tally: 7 🤩 vs. 9 🥱
From a raw feature standpoint, there’s almost nothing new about Wiz code - these scanners exist in other CNAPPs, and go unused due to their complexity and weirdness. However, Wiz’s offering here is genuinely unique and new because it excelled once again at the simplicity and usability of the user experience, especially from a security perspective.
The scanners themselves are nothing special. At this point a CNAPP announcing an SCA scanner gets me about as excited as someone saying they make attack paths - I’m more shocked they don’t have it than when they do. What matters is the actionability of the new data and how it surfaces in the product and to developers - most of which is the code to cloud changes.
The Good 🤩
Code to cloud is the holy grail of vulnerability remediation. There are a lot of ways to try and build this graph, but no matter how someone tries to do it, it’s really hard. Wiz deserves props for threading an elegant middle ground in making this usable, especially in the enterprise. The WizCLI scans in pipeline, scrapes metadata to associate the committer and repo, and tags the image (also counts as integrity checking). The tag is used to trace the container back to the repo that produced it. This isn’t the most advanced approach I’ve seen, but it’s one of the only ways to get a guaranteed match between a repo and a deployed container.
The UX of traversing multiple discovery sources. I found this simple switch on the vulnerability findings view to be an extremely elegant approach for navigating the different vulnerabilities. There is a massive complexity in navigating the nuances between code and cloud findings, and this simple toggle is a really smart approach.
The elegance of the policy engine. Wiz’s policy engine used to be really complicated to try and use, and didn’t sync well between the CLI and the cloud resources. Now that you can enforce policies as code, build, or cloud, it creates a much more intuitive experience
The approach to SAST (for a CNAPP). The hidden gem in this announcement is that Wiz is now ingesting vulnerabilities from other sources, with a standard way to send vulnerabilities into their platform. Wiz will have to be careful about data quality the further they go down this path, which is probably why only Checkmarx is an initial partner. Rather than shoving out a half-baked SAST, I think this approach makes sense if the data quality can stay consistent.
Unified product experience. Wiz’s integration of code into the wider platform is most apparent in the toxic combinations ingesting this new information like any other. Findings are prioritized based on if they’re seen in runtime, exposed to the internet, or used in a privileged container. It’s not just about the alerts themselves, but how natively the code context has been integrated into the broader approach.
The Lame 🥱
Code to Cloud requires a large investment to setup. Wiz’s code to cloud is a smart sales pitch because it’s offered as image integrity checking, but really is what ties the code to cloud picture together (this is Endor’s approach as well). This is okay, but is much less impressive than the innovation from vendors like Dazz, Opus, Phoenix Security, Cycode and Ox which attempt to make the association without any instrumentation. If you’re buying Wiz Code for this functionality, just know that a lot of setup will be required to see the magic.
The scanners themselves aren’t really changing much. The container scanner already picked up SCA findings, the CLI already scanned container images, and Wiz already scanned resources at runtime for secrets. Scanning the repos themselves is still important, but there’s really not much new information coming from these sources. Plus calling some of these separate scanners is a stretch - does anyone really need malware scanning in their repos? Help, my developers won’t stop pushing their laptop viruses into my git repos!
Edge Cases. Both for the code to cloud functionalities and the findings navigation, even in brief demos I was able to notice a little bit of funk. Whether CI/CD jobs showing as unknown, or component names showing indecipherable strings, the elegance of the pitch will be better than the reality.
We’re stretching by calling this another SKU. To be clear, from a market analysis perspective, I think Wiz is really smart to spin this as a separate SKU, and there’s just enough here to make it acceptable. But from an end user perspective, it requires a lot of storytelling to make it make sense. If you look at the raw functionality, it’s just a GitHub App scanning for results you already have. It requires really indexing a lot of value on code to cloud, and the PR & IDE integrations.
Who is this for?
I talk about a lot of very cool SCA vendors like Backslash who are doing some really cool things with reachability and extending it into SAST, or Arnica doing things with workflows that go beyond opening a PR. I like these tools a lot and think they’re better than the older alternatives; however, the reality is that most of the market uses Checkmarx, Snyk, or GitHub advanced security for SCA scanning. To me, Wiz Code is squarely aimed at stealing dollars from the Github advanced security license. Additionally, Snyk or Checkmarx customers will likely struggle to justify anything besides the SAST license - not that their other scanners don’t do some things better than Wiz, but they don’t do them better enough to justify the separate spend for most people. It’s no coincidence that just yesterday Snyk was pleased to share their Snyk Code revenue, something super out of the ordinary for them to do.
Wiz continues to meet the market where it’s at. I’m getting asked about SCA alternatives more than ever, and Wiz is giving a solution as most people are looking for it. If anyone asked me for “the best SCA tool,” I’d never recommend it, but if they already have Wiz, I’d suggest they consider it, and there’s a strong chance they’d buy it.
While it’s sad to see, a lot of people equate application security with SCA and Secrets at this point. These scanners are the most basic and noisy, but to a lot of the industry these two features are all they know about application security. In my experience and conversations, it’s always been way harder to sell the other 6 scanners.
Where does this leave ASPM?
Wiz calling this ASPM via SAST and DAST integration is really a stretch; not as much of a stretch as Snyk’s ASPM offering, but it’s up there. From a pure capabilities perspective, SAST is a major gap, and existing ASPM players have much more flexible integration options for doing holistic vulnerability management with different existing scanners.
Ultimately an ASPM should be built for developers, and this solution certainly isn’t. Wiz will tell you most of their users are developers, but it’s only because they’re forced to be by the security team to see their vulnerabilities. I’m not saying it’s bad from a company strategy standpoint, but I am saying that if I was a developer I’d prefer to use Cycode or Aikido to Wiz for my code vulnerabilities. But it’s worth remembering that developers aren’t usually the ones looking for vulnerability tools.
CNAPP has always claimed to do all of these things, and has never really delivered. Wiz is different in that it delivers more than their competitors; however, the capabilities and usability still lag dedicated ASPM players.
In summary, I really wanted ASPM to eat CSPM, since the code stuff is way harder and more important than the cloud side. Before Wiz code, I was more certain that this would happen, because most of the CNAPP platforms were totally unusable even before application context came into the picture. Wiz code is just good enough that it poses a real threat to ASPM holistically, but a lot will be in if the offering can evolve at the rapid pace Wiz has maintained so far. However, the immediate change in the market will just be slightly fewer people looking outside of Wiz for a complementary AppSec solution, since I would agree that Wiz Code is “good enough” for most people getting started in AppSec. In my opinion, it represents the only real medium term challenger to ASPM from a CNAPP, not the end of AppSec tools.
Conclusion
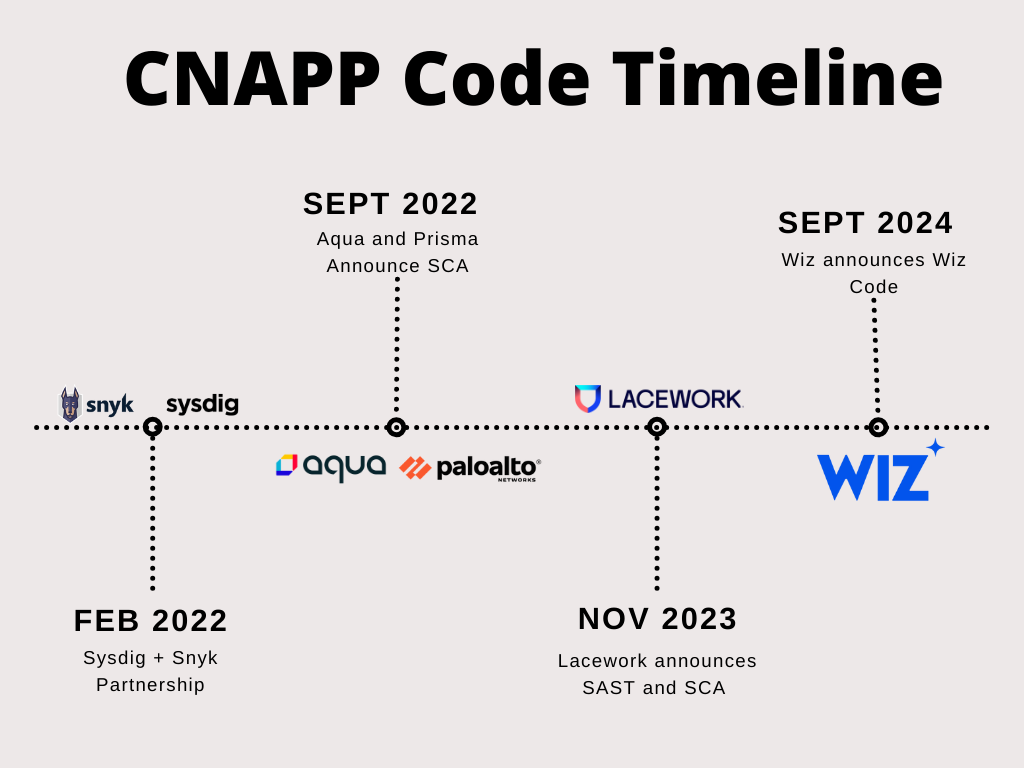
The above graph is a billion dollars worth of advice, especially if you remember that Wiz was also the last major CNAPP to market. Here are some dates to ponder:
Sysdig and Snyk partner for runtime reachability in February 2022
Aqua announces SCA and SBOM in September 2022 and I’m not sure the date SAST was added
Every major CNAPP player beat Wiz Code to market by a period of two years, and yet not a single person messaged me about it, or was at all concerned about the demise of AppSec. Having a cohesive and understandable product offering is far more important than having the first one to market.
With Wiz Code, Wiz has proven once again:
Marketing and brand matter. Not a single person asked me about the Lacework SAST + SCA announcement, even though I posted about it. For the haters, part of Wiz having a good brand is that you don’t often meet users raging about Wiz’s product the same way you can with…other vendors.
Satisfying end users > satisfying analyst spreadsheets. Wiz code is a cohesive part of their product, not some new scanners getting bolted on to a new sidebar dropdown. This offering is impactful primarily because it’s not the seventeenth dropdown on a use case sub-page.
Execution > time to market. Wiz continues to do a great job, and they don’t show any sign of slowing down. This sucks because it means I have to keep posting about them and get yelled at by everyone for being biased. I’m sure some big threat detection announcement is up for Q2 next year. (For clarity, this is a total speculative guess, I have no actual information about a threat detection announcement; however, it’s the last infinity stone needed to go full Thanos with CNAPP, so I’m assuming it’s happening, and surely the Gem folks are doing something to stay busy besides making money snow angels).
TL;DR at the bottom: Wiz Code is the best offering from a CNAPP, better than some legacy scanners, but not as good as modern ASPMs.





Great article James! Thanks! Minor fix, you missed a 'c', it says 'between code and loud findings'. The article says, "The UX of traversing multiple discovery sources. I found this simple switch on the vulnerability findings view to be an extremely elegant approach for navigating the different vulnerabilities. There is a massive complexity in navigating the nuances between code and loud findings, and this simple toggle is a really smart approach."
All the good points, although why are you downplaying the risk of malware in code? Abusing org repos for malicious hosting is a real risk, but also the supply chain angle of malware in the code.