Wiz Defend-ing Their Flank
An early preview of Wiz Defend, and the next 5 years of runtime focused CNAPP
Special thanks to the Wiz team for giving me an early briefing of their Defend public preview. They did not sponsor this article in any way.
Wiz code was an impressive entry into Application Security Posture Management (ASPM) from a Cloud Native Application Protection Platform (CNAPP) provider precisely because every other CNAPP had stumbled into the space so disastrously. Without re-hashing the article, Wiz Code was the first strong entry into application security from a CNAPP provider because it successfully leveraged surfacing code vulnerabilities within a cloud context.
Wiz Defend represents a different market than Code, one where there is much stronger competition from CNAPPs. In my experience, Wiz’s weakness has always been runtime protection. Aqua, Sysdig, and Prisma (Twistlock) have a much longer history in the container runtime protection arena, and there are several new and smaller providers with genuinely innovative solutions. In prior roles as a security engineer, I have at times selected other platforms over Wiz for precisely this reason. More importantly, the new generation of cloud security providers like Upwind, Sweet, ARMO, and RAD have all focused on their runtime detection engines, aiming to go beyond where those like Aqua and Sysdig started. Between recent Sysdig leadership changes, and Upwind’s recent fundraising round, runtime is at the center of the next 5 years of CNAPP.
In this article, we’ll cover the history of Wiz creating this offering and why it’s critical to their long-term success. We’ll then cover the good and disappointing aspects of it from a product perspective. The TL;DR? Wiz Defend, in its early preview stages, is a good step in a necessary direction for the company, but aside from one major advantage, it continues to be the weakest point of the platform. However, the weakest point of a strong platform is still pretty good.
Brief History and Future of Wiz and Runtime
Back in June of 2023, Wiz launched their runtime sensor. As Francis and I identified in our CNAPP report, this is one of a few pivotal moments in Wiz’s history. Let me be frank: I love runtime Kubernetes protection. I think it’s the single most important feature of these platforms, and I always have - it’s where real visibility and defense potential lies. You will never resolve every vulnerability, so runtime protection will always be necessary. Every other aspect of CNAPP is a work generator, runtime protection is the only thing that truly does something for you.
Wiz launching their sensor is the reason I have been able to recommend and talk about them so often compared to Orca - the agentless visibility is important, but runtime protection is a gap that cannot be allowed to exist in modern cloud environments. Put differently, for as much as I might get accused of being a Wiz fanboy, if the agent didn’t exist, I wouldn’t be personally interested at all in Wiz. Furthermore, the Wiz sensor has always had pretty good detections. When it launched, it lacked some SOC first features like response actions and custom rule engines, but built up detection capabilities on par with most major container security solutions and quickly became a competitive offering. It was way better than legacy EDR’s embarrassing attempts to enter this arena, but wasn’t quite as good as the dedicated players.
Because Wiz was so late to market with an agent, I was surprised when Wiz chose Gem to acquire and build their runtime defense product. To be sure, Gem had amazing cloud detection content, and a strong anomaly detection engine that I saw as the fulfillment of Lacework’s vision; however, Gem did not have an agent, and had very little visibility inside of Kubernetes workloads. I thought that was a big gap - and still have the Latio list description to prove it! Talking to the Wiz team more recently, this was actually precisely why they purchased Gem: Wiz is confident that they have the best people working on their sensor that they wanted Gem to build up the agentless detections.
Now, just 8 months later (seriously amazing engineering work from the Gem team to rebuild the product in such a short time), Wiz launches Defend at an absolutely critical moment. The market demands enhanced runtime protection for their workloads, as they face disillusionment with "shift left” and endless vulnerability scanning. Security practitioners want greater visibility into their cloud applications, and to feel safe without creating ten million tickets. For example, the partnership between Aqua and Orca highlights areas where their offerings complement each other, even though both aim to provide comprehensive solutions. The reality is that security teams start with agentless visibility, and then move into agent based runtime protection, and that most CNAPPs are only really good at one or the other.
Another historical awkward turtle for CNAPP has been lack of Windows support. For a lot of organizations, this meant splitting runtime alerts between CrowdStrike or SentinelOne for Windows, and their CNAPP for containers. Unfortunately, this gave EDR players a huge advantage to expand into containers. Part of the Wiz Defend preview is a private preview for the Windows sensor, another essential feature for keeping the cloud out of CrowdStrike’s hands (talons 🙄), allowing them to join the few cloud players that have a Windows agent.
In order to stay competitive, Wiz needs to absolutely nail the Defend offering for several reasons:
Their competition is evolving out of “the CNAPP wars” and into the big public company ones - namely Palo and CrowdStrike - both of whom thrive in Security Operations Centers (SOCs).
Wiz has come to dominate “cloud security,” but CNAPP has never done well in the SOC for two reasons: its emphasis on detecting misconfigurations rather than attacks, and the average SOC practitioner struggling to transition into a container first world.
In my opinion, while CrowdStrike is well-integrated in the SOC, their cloud/container offerings don't compete well against CNAPP providers.
For Cloud Native startups without legacy infrastructure, it is much easier to recommend newer players who have focused on runtime instead of large and costly CNAPPs.
Wiz scaling their pricing into the Palo/CrowdStrike stratosphere requires customers to view the Sensor and Defend as separate products from the “visibility” of agentless scanning - that means those products must compete on their own merit.
I continue to be skeptical of having runtime protection and vulnerability management in the same tool. Developers and SOCs fundamentally care about different things - a SOC threat response has a different timeline than patching a vulnerability. The mitigation must come from the agent, not from a patch!
Now that we know the stakes, does Wiz Defend stick the landing?
Breaking Down Wiz Defend
Wiz Defend can be separated into four “newish” features. I’ll go through each of these in more detail of what makes them cool or not.
🥱 = Boring, 🤩 = Dope, 🫤 = Mixed Feelings
New Readiness Dashboards
Extending the “Boards” concept into threat detection widgets showing open alerts and MTTR 🥱
Incident Readiness dashboard showing log coverage 🥱
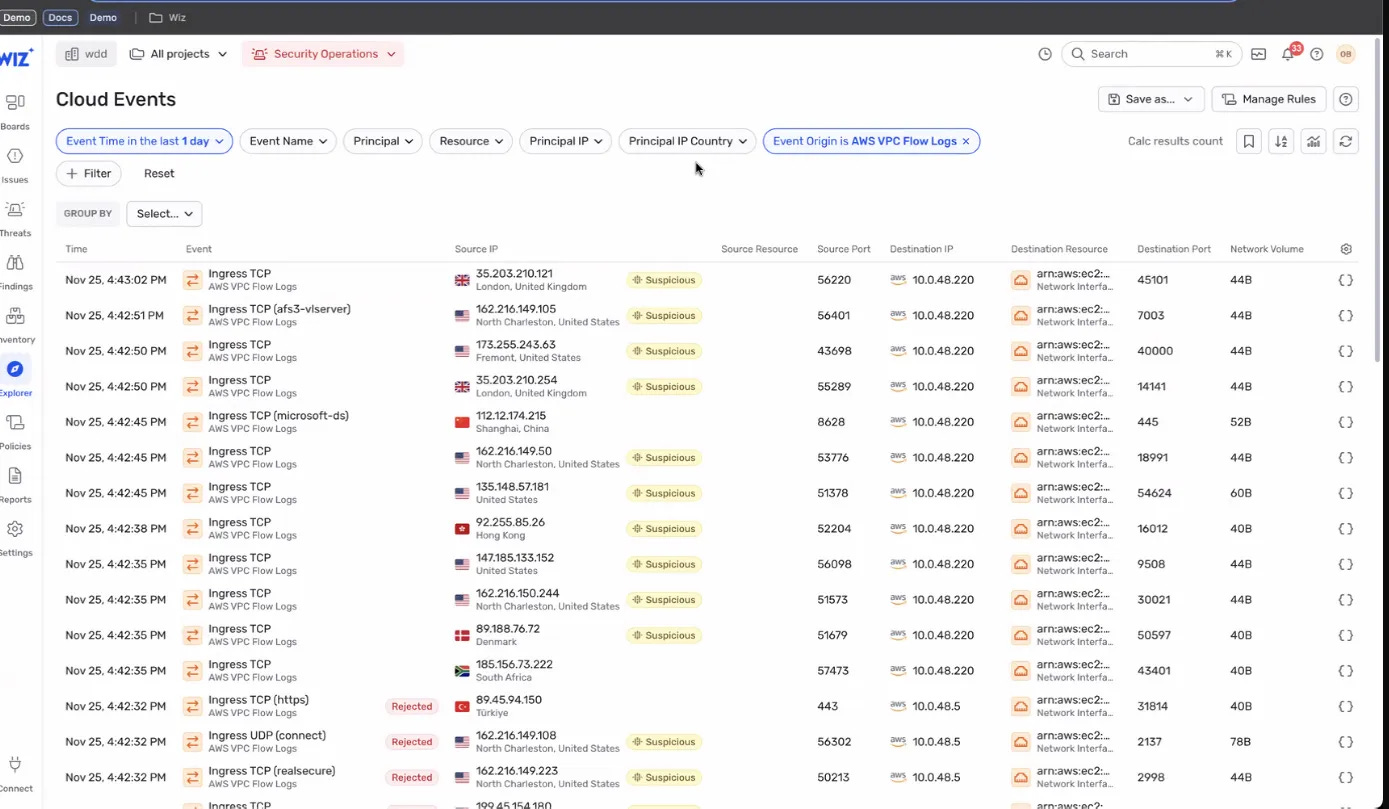
Basic event filtering and searching
Existing filtering for cloud events, but new filtering for sensor events 🥱
Extended support for different cloud log types 🥱
Baselining cloud detection rules & responses
Bringing Gem’s cloud attribute baselining to Wiz 🤩
Some baseline detections for containers 🫤
Cloud response actions - like revoking roles 🤩
Workload to Cloud runtime detections
Combining detection events across workloads and cloud events 🤩
Basic pivoting on principals from the alerts🫤
Totals: 3 🥱, 3 🫤, 3 🤩
In sum: there’s some cool things happening, but this isn’t everything a SOC needs in order to be effective at cloud security. But it’s also treading the line of being an augment to an existing SIEM detection stack, and being a proper standalone solution for cloud native architectures.
A very quick aside before getting into the rest of this analysis: my opinions on these features are from the context of using Wiz Defend as the single source of truth for runtime security alerts in the cloud. How to interpret this feedback depends a lot on who the competition is - some of these features are lightyears beyond some CSPMs, but are lagging behind others. I don’t go into detail about which is which, but will address the competitive landscape at the end.
New Dashboards
Unlike Wiz Code, which melds well with existing search and dashboarding concepts in Wiz, the Wiz boards don’t fit as well with security operations. Anyone who’s worked in a SOC knows that these dashboards can get very complex and multi-faceted, with different teams needing different views, sometimes related to alert metrics, SIEM health, or CISO dashboards.
The two new dashboards I saw were “Security Operations” and “Incident Readiness.” These dashboards are right in concept, but they’re lacking the data lake type of searches and functionalities a SOC might use for threat hunting or team performance tracking. Below I’ve included the Incident Readiness page compared against Splunk’s as an example, or because I’m familiar with it, the model index page from MDR provider, ReliaQuest’s GreyMatter. Both of these dashboards are trying to give SOC users and leaders the metrics they need to track operational health. The Wiz dashboards are a step in the right direction, but are far from empowering a “Cloud SOC.”
Comparing the Wiz SOC dashboards to purpose built tools:
The Wiz dashboards are a good start, but don’t give the full scope of necessary functionality to truly run cloud security operations.
In the SOC, one of the most important data points is log source coverage. In Wiz Defend, log collection findings are treated as CSPM style findings, and log sources are just different cloud event sources. Combined with MITRE ATT&CK coverage, this is the right dashboard in theory, but it’s so limited to cloud log sources, and ATT&CK is so overrated by CISOs, that it’s not something I see practitioners spending much time looking at.
Overall, these dashboards are okay, but they’re far from the level of detail SOC personnel are used to from SIEMs or EDRs.
Event “Searching”
The biggest issue with Wiz Defend will be the lack of maturity for searching through cloud and container logs during an investigation or threat hunt. One example I was shown was a process on an EC2 instance taking an unusual read action on an S3 bucket. I’ll have more to say about why that detection is cool in the next section, but I can’t imagine the log filtering experience to be a fun time. While the attack timeline is important, it typically opens questions that only advanced searching can answer.
To be clear, this is not an issue only with Wiz, most CNAPP providers outside of Sysdig do not have adequate search capabilities across container agent logs. Introducing the Runtime Events search is a key step in the right direction, but in its current state seems to be less usable than alternatives.
The workflow around searching feels currently underbaked, but with a lot of potential - the timeline view and investigation graph surface the key logs during an attack; however, anyone who’s been in a SOC knows that these surfaced logs are just the beginning of the robust searching necessary, often across multiple event sources.
Detection and Response Capabilities
First, the team at Gem is incredibly talented at creating cloud based detections. Some examples I noticed from the demo were:
Identifying suspicious VPC flow log patterns (anyone who’s tried knows how nightmarish and expensive this is to try to do yourself via a SIEM)
Identifying unusual cloud access patterns
Tying access abnormalities across Okta and AWS control planes
Data perimeter type detections - such as AWS credential usage outside of your accounts
These are all the classical “CDR” detections (i.e. cloud control plane level alerting) that Gem was really strong at, and they continue to be good here. For the alerts involving cloud layer logs like S3 and VPC, I’m confident they will be high quality.
Before I continue, let me say that all of this analysis should come with a grain of salt. I’m extremely hesitant when endorsing anomaly based detection mechanisms, because they’re notoriously noisy and full of false positives. Everyone in the CNAPP world can say “we do anomaly based detections!” but I’ve been extremely disappointed by most of them. Nonetheless, the results here seem promising.
One part of Defend I really liked were the new response actions for cloud level detections. Being able to revoke sessions or place a permissions block on the role are all useful responses. Conversely, it seems that the sensor response actions are still only the ability to kill a malicious process, which is quite limited compared to some advanced quarantining ability I’ve seen from Rad and ARMO specifically.
Workload to Cloud runtime detections
Saving the best for last, the new investigation graph is at the heart of the potential of Wiz Defend. Correlating cloud alerts to container ones is extremely challenging work. To use the above image as an example, there’s no necessary relationship between S3 read and the container process, so tools have to use complex and proprietary mechanisms to relate these to one another. Wiz is now only one of four tools where I’ve seen this sort of correlation in action. It’s worth noting I have never been hands on with any of the four to verify that it actually works! But the other three are Upwind, Sweet, and ARMO. That said, In this specific example from Wiz, it seems that the correlation may not be as direct as it appears.
Let’s really map out the above example: imagine an attacker has remote code execution (RCE) to a container, they use the RCE to steal data from S3, and ship it to their attacker server. That’s sort of what this investigation is showing, but it’s faking a little bit. The Wiz graph is showing me that the RCE happened, and connected back out to the attacker server. It’s also showing me that the EC2 host made an anomalous read to an S3 bucket using its instance role. It’s then associating those events together, likely because the cloud graph sees them as related assets with malicious events.
In reality, the graph should look a little bit more like this one from Sweet Security, where it shows the user assuming a role, exec’ing into a pod, running an AWS command, the new role that command is using, and the action it took against a cloud resource. Based on the demo I was shown, it appears that the Wiz graph isn’t actually aware that the particular process took the read action, only that a container on the host did.
That small distinction aside, this workload to cloud alert correlation is absolutely essential for making the idea of cloud detection and response a reality. For too long these runtime detections have been totally uncorrelated, leaving practitioners unable to determine if an attack is successful, or if two different alerts are related to one another. This “workload to cloud” (“Wiz Sensor” to “Wiz Defend”) capabilities is the heart of the innovation happening here, and is the first step towards evolving CNAPP runtime capabilities. This is feature is also the new standard for CDR tools.
Should you buy Wiz Defend?
Let me start with a disclaimer - runtime tools demand especially thorough testing which I haven’t done for every tool I’m about to talk about. So that you know my biases, I’ve recently (one year or less) used/evaluated Wiz’s sensor, CrowdStrike, Palo, Oligo, ARMO, and Rad, so I feel comfortable in what I’m saying with them. I’m over a year out from my last hands-on time with Sysdig and Lacework. I have not been hands on with Miggo, Raven, Sweet, or Upwind (but have gone through several in depth demos with real world attacks), so take those recommendations with a grain of salt. Conduct your own thorough testing and I’m open to being proven wrong!
Evaluating Wiz Defend from a purchasing mindset requires breaking down CNAPP more than I usually do into five categories:
Versus behemoth incumbents: Prisma and CrowdStrike (Fortinet? SentinelOne?)
Versus container runtime incumbents: Sysdig and Aqua
Versus pure CSPM, or agentless CDR: Orca, Stream, SkyHawk
Versus cloud runtime first companies: Upwind, Sweet, Rad, ARMO, Operant
You’re already a Wiz customer and evaluating the SKU
First, is Wiz Defend better than Prisma and CrowdStrike? I’m confident that the detection experience for supported workloads will be vastly superior to both. My personal hands on experience comparing the Wiz and CrowdStrike sensor early this year led me to conclude that Wiz’s is far superior, and I’m speculating that it especially extends to the cloud control plane alerts. While Twistlock has kept Prisma’s runtime competitive for a long time, it’s overdue for some tender love and care. From an investor or overall company success standpoint, this first point is the most important.
Second, is Wiz Defend better than incumbent runtime oriented solutions? Whereas it was easy to say that Wiz Code was a standout offering against other CNAPPs, Wiz Defend doesn’t have the same luxury. There are some marginal pros and cons when comparing Wiz Defend to incumbent CNAPPs like Aqua and Sysdig, but they’re roughly comparable overall. The biggest pro for Wiz is some amount of correlation between cloud and container alerts. The biggest con to Wiz is the usability and flexibility of logs, detections, and responses. The challenge here for the incumbents is that their detection experience is now a toss up (at a high level without thorough testing), when the rest of the platform experience generally favors Wiz.
Third, is Wiz Defend better than agentless CDR? I believe it will be - both because it has an agent, and because I trust Gem’s pedigree at the cloud anomaly stuff, worst case scenario it will be good enough that it’s not worth buying a separate CDR that’s only agentless.
Fourth, is Wiz Defend better than “Runtime First” players? No - these companies are exploring innovative approaches that, in my view, set them apart from Wiz Defend. From flirtations with ADR and API Security, to robust container runtime anomaly detections, these guys are all doing cooler and more meaningful stuff for runtime oriented security nerds like me, pushing the boundaries of eBPF and other detection mechanisms.
Fifth, should you upgrade to Wiz Defend? Part of that is how much Wiz charges for it. Obviously, at a high level, this is an upgraded capability that matters for securing your cloud. If you’re only ever going to use one tool for cloud security, yes this upgrade seems worth it. If you’re evaluating CrowdStrike or Prisma, yes it seems you should do Wiz instead. But if you’re willing to evaluate a runtime specific tool for this, it’s what I would personally recommend.
In summary, Wiz Defend is a competitive offering, but it’s one that’s hard to recommend in isolation. It’s the first offering from Wiz that doesn’t automatically win the category it’s in; however, it’s also shoring up the weakest part of the platform, continuing Wiz’s dominance in the CNAPP category. If your vision of CNAPP includes all in one support for cloud asset scanning, code vulnerability management, and cloud runtime protection - Wiz remains the leader in that complete CNAPP vision.
However, if you want the best runtime protection for cloud workloads, Wiz Defend by itself is more a contender than the clear winner. That said, it seems way better than the mainstream choices most CISOs are plugged into - namely CrowdStrike. That leaves it with one use case, being part of a platform that is holistically better than the other platforms. That will sell just fine, but I’m personally not all that excited about it. Wiz Defend is a great choice if you’re unwilling to go outside of CNAPP for your runtime protection.
What’s really needed in this space is some objective testing, which Latio should provide soon, so don’t forget to subscribe!
A brief aside because it didn’t really fit anywhere else: the go to market with defend seems heavily invested into the MDR and SOAR ecosystems which is really smart. A lot of those guys have a bone to pick with CrowdStrike who now sell their own managed services a lot, and it’s a great on ramp into the SOC for many companies who are dependent on their MDR for runtime.












Hey James, How can we bring together Platform Security engineers and Secops? Traditionally the two personas operate in silos. This makes threat investigation and forensics difficult. I would love to hear how to integrate runtime threat detection in CNAPP products to provide value to CNAPP consumers. Is this through more context and correlation, or do we need to think of new workflows in CNAPP?
Of the pure-play runtime vendors, which would top your list? We've had the unfortunate experience of being on CrowdStrike's cloud SKU since '21 and it's been horrible. We adopted it mostly for runtime given our MDR engagement with the Complete team. We're actively exploring Orca and Wiz at the moment for CNAPP and mid POC the Defend product dropped. It's a bit too earlier for me to consider given the recent release (v1), but your article did make me think more about exploring a pure-play runtime vendor.